Recover Hacked Facebook Account in 2025 — 10 Proven Steps to Regain Control Fast
Recover Hacked Facebook Account in 2025 — if your Facebook account has been compromised, follow this prioritized, practical guide. It’s written for speed and clarity: quick actions first, detailed recovery next, then permanent hardening. The techniques reflect Facebook’s current recovery options and modern security practices in 2025.
Quick checklist: regain access now
If you need to Recover Hacked Facebook Account in 2025 fast, do these immediate steps in order. They are prioritized to maximize success with minimal friction.
1 — Start at Facebook’s official recovery page
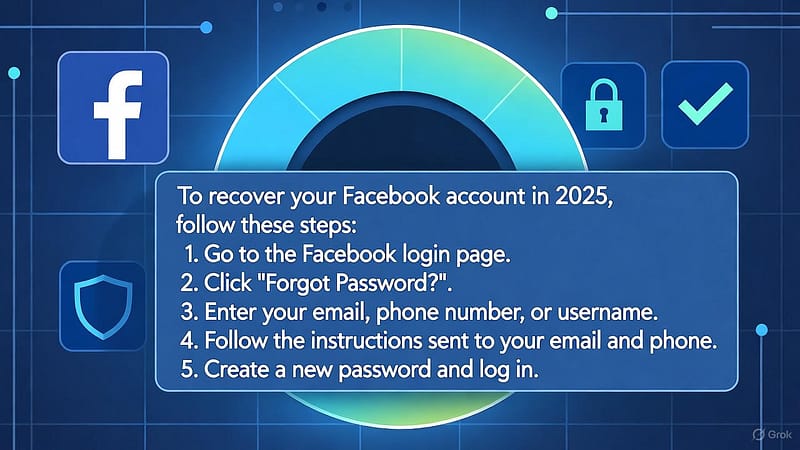
Go to facebook.com/hacked. Follow the guided prompts to detect compromised elements and begin recovery. Using this route first reduces manual paperwork later.
2 — Try “Forgot password?” with known email/phone

Use facebook.com/login/identify if you still have access to the linked email or phone. Reset passwords from emails that originate from @facebookmail.com or official Facebook addresses only.
3 — Inspect email for Facebook security messages
Search your inbox for “Facebook” and check for security notices or messages about recent changes. If you see messages about password changes you did not make, follow the recovery links (not links in random posts).
4 — Log out unknown sessions when possible
If you regain access, immediately go to Security → Where You’re Logged In and remove unknown devices. Then change your password.
5 — Use trusted contacts or ID upload when required
If you cannot use email/phone, Facebook may allow trusted contacts or an ID upload. Follow instructions carefully and use clear, accurate documents to speed verification.
Step-by-step recovery
This section expands the quick checklist. If the first set of actions didn’t work, follow these more detailed tactics to recover your account and verify ownership.
Understand the attack surface
When attempting to Recover Hacked Facebook Account in 2025, first assess how the attacker gained access. Common vectors: phishing links, reused passwords, compromised email, malicious third-party apps, or SIM swap attacks. Identifying the vector helps choose the right recovery path and prevents immediate re-entry by the attacker.
Use official recovery workflows
Facebook’s primary recovery flows (facebook.com/hacked and facebook.com/login/identify) are optimized for the most common situations. When you use them, Facebook records device and location metadata that can speed verification. Stick to official pages; attackers often create convincing fake forms.
Recover if the email or phone was changed
If the attacker changed your contact info, use the “No longer have access to these?” flow inside the recovery process. Facebook may ask for a secure ID upload (government ID, passport) or allow verification via trusted contacts if you set them up previously. Carefully follow the instructions and ensure uploaded images are clear and within Facebook’s file requirements.
Prove ownership without email
When email or phone access is impossible, you may be asked to submit:
- A government-issued photo ID (ensure the name and photo are visible).
- Copies of account-related documents (e.g., Page business verification) where applicable.
- Details of recent actions only you would know (login locations, ad account IDs).
Accuracy matters: mismatched or low-quality documents slow the review process.
Protect your recovery email account
Attackers often control Facebook by first controlling your email. To Recover Hacked Facebook Account in 2025 successfully, immediately secure the email account used for recovery: change its password to a long, unique passphrase, enable two-factor authentication, and review its active sessions and forwarding rules.
Revoke malicious apps and sessions
Once you regain access, go to Settings → Apps and Websites and remove any suspicious apps. Then sign out of all sessions and change passwords for both Facebook and any linked accounts (email, cloud storage). That reduces chances of a stealthy re-entry.
When to escalate to Facebook support forms
If the automated flows fail, use Facebook’s Help Center forms for compromised accounts or pages. Provide clear, factual descriptions and attach requested proof. Keep reference numbers and follow up if necessary; persistence can be required for complex cases involving Pages or ad accounts.
If two-factor authentication or contact info was changed
When the hacker enables 2FA, standard recovery becomes harder. Do not panic—Facebook has built verification paths for these scenarios.
Options when 2FA blocks you
- Use recovery codes (if you saved them previously).
- Try logging in from a previously used device or IP—Facebook sometimes soft-trusts familiar devices.
- Submit an ID verification if Facebook prompts for it.
Follow the exact steps Facebook requests and be sure to respond using the email address you control. If you are repeatedly denied, double-check your submitted documents for legibility and that personal data exactly matches your account details.
Recover Pages, ad accounts, and business assets
If attackers gained access to a Facebook Page or ad account you manage, this escalates the risk and complexity. For Pages, use the specific recovery routes in Facebook Help Center for Pages and Business assets. When recovering Pages:
- Collect admin evidence: screenshots showing your admin access before the hack, invoices for any ad spend linked to the Page, or business registration documents.
- Report the Page as compromised using Facebook’s Page recovery forms and include as much proof as possible.
- Coordinate with any co-admins who still have access so they can remove the intruder.
For ad accounts, be ready to verify business ownership and contact Facebook Business Support if you have access to Business Manager. Document fraudulent charges and request refunds where appropriate.
After recovery: lock it down permanently

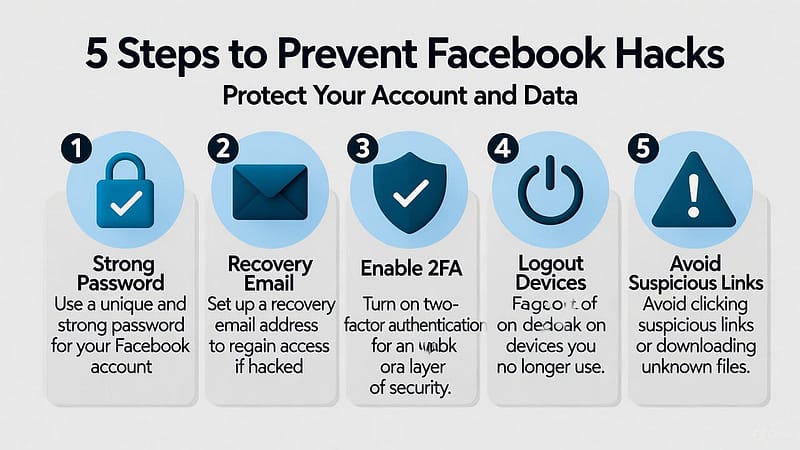
Once you successfully Recover Hacked Facebook Account in 2025, follow a clear hardening checklist to ensure attackers cannot return.
Password and authentication
- Set a long, unique password—use a reputable password manager to generate and store it.
- Enable two-factor authentication using an authenticator app (not SMS) or a hardware security key for the strongest protection.
Review email account health
Secure the linked email account: remove forwarding rules, set strong credentials, enable 2FA, and check recovery options. Attackers who control your email can break Facebook controls again.
Remove risky integrations
Revoke permissions for third-party apps, especially those requesting broad access. Minimize app permissions to the least necessary.
Audit friends and posts
Check for messages, posts, or friend requests sent by the attacker and notify contacts if they might have been targeted. Delete malicious posts and, if needed, report scams to any affected parties.
Set login alerts
Enable notifications for unrecognized logins. This provides immediate awareness if someone attempts to access your account again.
Prevent future hacks — practical, high-yield actions
Prevention is the most reliable way to avoid the headache of recovery. These measures stop common attack vectors used in 2025.
Use a password manager
Password reuse remains the most common cause of social account takeover. A good password manager eliminates reuse and makes long unique passwords practical.
Prefer authenticator apps and security keys
Authenticator apps (TOTP) and FIDO2 security keys are much stronger than SMS. Use them wherever possible.
Harden your email
Because account recovery depends on email, that account should be secured at the highest level: strong password, 2FA, and removal of legacy recovery options that could be abused.
Beware of phishing
Train yourself to inspect URLs and sender addresses. When in doubt, go directly to the official site rather than clicking an email link. Use browser protection and anti-phishing tools.
Minimal third-party access
Grant third-party apps the least privileges needed. Regularly audit app permissions and remove anything unused or suspicious.
Device hygiene
Keep OS and apps updated, avoid pirated software, and use a reputable mobile security product if you suspect compromise. If a device is suspect, factory-reset after backing up essential data.

Tools and resources
Below are official Facebook recovery links and helpful external resources you can trust when trying to Recover Hacked Facebook Account in 2025:
- facebook.com/hacked — official recovery tool
- Recover a hacked account — Facebook Help Center
- Recover a hacked Facebook Page
- how to stop phone from overheating (useful if device compromise is suspected)
- Social Media Privacy 2025 — internal analysis
- Social Media Algorithm Changes 2025 — internal analysis
Tip: bookmark Facebook’s official recovery pages and your email provider’s security pages for quick access during an incident.
Advanced Recovery Tips: When Standard Methods Fail
If you’ve tried every step and still can’t recover hacked Facebook account, don’t panic. Some advanced recovery methods may still help you regain control. Start by checking your Facebook account’s login history through “Security and Login” settings. If you can identify a region or IP address that doesn’t belong to you, report it directly through Facebook’s compromised account form. This helps Facebook prioritize your case in their automated systems.
Next, attempt to recover hacked Facebook account using a trusted device you’ve logged in with before. Facebook’s AI-based recovery flow recognizes device fingerprints, making the process faster. Always make sure your browser cache and cookies are intact, since deleting them might reset the trusted device signals.
If the hacker removed your personal data (name, email, or photos), upload an official ID when prompted. This confirms your identity and helps Facebook’s automated verification system. Using a secondary, secure email for communication with Facebook Support is also recommended during the recover hacked Facebook account process.
Prevent Future Hacks After You Recover
Once you successfully recover hacked Facebook account, your job isn’t done. Prevention is your best defense. Always review your recovery settings monthly. Update your password at least twice a year and make it long, random, and unique to Facebook.
Check your authorized apps under Settings → Apps and Websites. Remove any integration you no longer use. Attackers often hide malware in third-party login permissions. When you recover hacked Facebook account, immediately disconnect apps you don’t recognize to reduce the risk of re-hacking.
Finally, learn from security updates shared in trusted tech sources. You can also read our related guide on Social Media Privacy 2025 for insight into how evolving privacy settings can protect your Facebook from future attacks.
Understanding Why Facebook Accounts Get Hacked
To recover hacked Facebook account effectively, you first need to understand how hacking happens. Most cases begin with phishing links or fake login pages that steal your password. Others come from leaked credentials found in public data breaches.
Hackers also exploit weak or reused passwords. If your password is used across multiple sites, an attacker who gets your credentials from another service can easily log into your Facebook. When you recover hacked Facebook account, make sure to use a brand-new password that isn’t reused anywhere else.
Lastly, keep your devices secure. Outdated software, unpatched browsers, or risky apps can expose your account. For a full guide on device maintenance, see our partner article on how to stop phone from overheating, which also discusses hidden background apps that may signal malware.
How Facebook’s Security System Has Improved in 2025
Facebook’s 2025 update introduced new recovery tools that make it easier to recover hacked Facebook account. The platform now uses AI-assisted recovery paths and device verification to quickly authenticate real users. This means if you’ve previously logged in with your smartphone, Facebook can identify you even if your password changes.
These improvements also help reduce wait times for manual ID verification. Users who upload valid identification now often regain access within a few hours. This advancement proves that it’s more efficient than ever to recover hacked Facebook account compared to past years.
Facebook’s updated system even notifies you of suspicious login attempts and recommends real-time password resets. The key is to act fast—speed matters in every recover hacked Facebook account situation. Don’t wait days before reporting the breach; the quicker you respond, the more data you save.
FAQ — Recover Hacked Facebook Account in 2025
How quickly can I recover a hacked Facebook account?
Many users regain access within hours when they still control the email or phone. If identity verification is required, it may take 24–72 hours depending on the region and Facebook’s review queue.
What if the attacker changed my email and phone?
If contact details were changed, use facebook.com/hacked and the “No longer have access to these?” flow. Be prepared to upload ID and provide supporting evidence to prove ownership.
Will Facebook restore a hacked Page I manage?
Yes—Facebook has Page recovery forms. You’ll need proof of admin status such as invoices, admin screenshots, or business registration documents. Provide as much accurate detail as possible.
Should I notify my contacts if my account was used to send scams?
Yes. Inform contacts about potential phishing messages and ask them to ignore suspicious links. Public posts may also be used to warn followers if your account was posting malicious content.
Can I speed up Facebook’s review process?
Always provide clear, legible documentation and respond to requests promptly. Using previously used devices or networks during recovery can sometimes speed automated verification.

Conclusion
To Recover Hacked Facebook Account in 2025 successfully, prioritize official Facebook recovery flows, secure the email you used for recovery, and follow a strict hardening checklist after regaining access. The combination of rapid action and long-term security measures (strong passwords, authenticator or security keys, minimal third-party access, and device hygiene) prevents re-takeover and reduces the damage if compromise happens again.
Keep a recovery plan ready: know the official recovery URLs, keep a secure copy of backup codes, and use a password manager to prevent reuse. Implementing these steps makes recovery faster and far less painful.